Protecting your mail like a PRO !!!
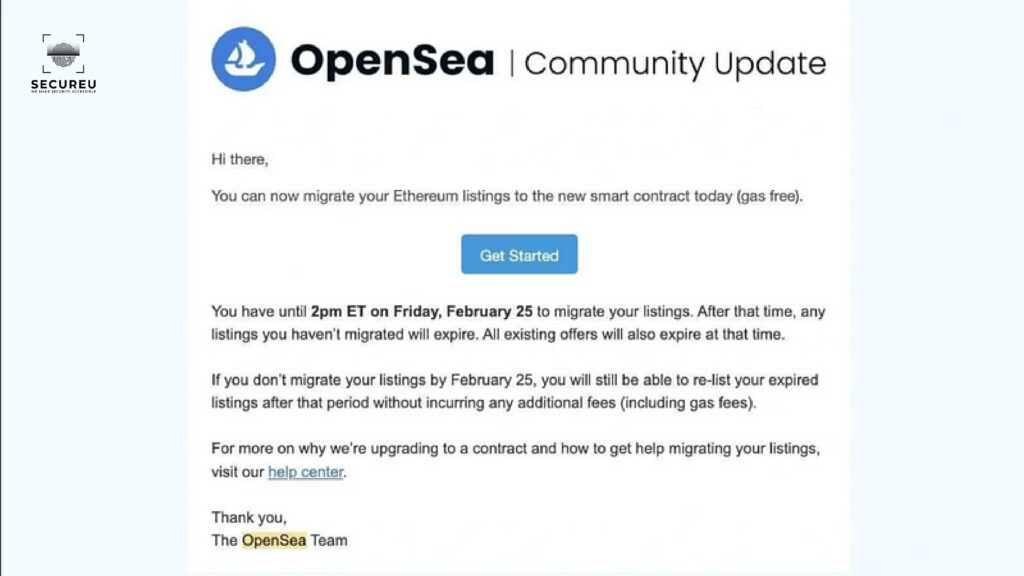
Protecting your mail like a PRO !!! To be true as a tech enthusiast who has been tinkering around with computers longer than I can remember, typing out this blog seems kind of ridiculous. I nearly moved away from my desk and had dropped the idea of writing this but then this happened. The podcast that I listen to occasionally started discussing the hacks that have been going around. You might say it’s a coincidence but right then they started discussing this major email-based phishing attack that was carried out against OpenSea users who bought NFTs on their platform. The attackers had sent an email to the customers of OpenSea that seemed legit at first glance and asked them to migrate their listings with the added bonus of gas-free transactions. If you know anything about the crypto world you know that gas fees (the cost of computing to carry out a transaction) can be pretty high and this bait of “gas-free” migration tempted users to fall for the trap and they ended up losing their NFTs. The total amount of the NFTs that was lost was worth around 1.7 million US dollars. It was then that I realized no matter how many blogs are already up there on the web regarding this. I am going to write one more, to maybe better educate my regular blog readers. Why does phishing exist in the first place? It’s 2022, on one side tech folks are busy creating Web3.0 infrastructure and then there are people still falling for phishing attacks that belong to the Web1.0 days. This begs us to ask the question why do phishing attacks still work in this day and age? People need to understand that email-based phishing attacks still exist cause email as technology was built with trust as an inherent factor. It was built in the early days of the internet when there were only a handful of people using it. They never saw the potential of what email could be and hence they never developed it keeping in mind the millions of spam emails that traverse the internet on a daily basis.It would have been fine if only that was the issue, but then comes in the other reason that’s a bigger contributing factor to why phishing attacks still persist. The reason is that we humans as a species are by default encoded to trust others rather than be suspicious of them. It is only after several mishaps that we learn that goes against our nature and start being suspicious of things that happen around us. So if you ever find yourself shocked by listening to the extent of phishing attacks that are still prevalent in 2022, remember the points that I just mentioned above. “I won’t fall for it” syndrome! One other issue that I have faced when it comes to phishing attacks is that people somehow disregard other peoples’ experiences and think that for some reason they are not vulnerable to such attacks and will easily be able to detect them. Now, read the next few words very carefully. “You are as likely to be vulnerable to a phishing attack just like any other person on this earth”. Please get rid of the “I won’t fall for it” syndrome. People who have written books on phishing attacks and such schemes have failed to detect phishing attacks and fall for it themselves. Side Note: I myself have been duped of a hefty sum of money. They used one of my shortcomings against me. I was unemployed at the time and they somehow managed to convince me to pay them upfront as they can help me land a respectful job. Thinking about it today makes me laugh at how I could have fallen for it. So, trust me when I say greed & fear will somehow make you do things that you can’t even imagine yourself doing in the future. So let me reiterate that it is only when you understand your own shortcomings that you have any chance to securely navigate through the spam and malicious mail that floods your inbox on a regular basis. Now let’s try and find a solution for it! What should we do then? I am glad you asked, now that you properly understand why phishing still exists. Let’s dive into how can we really eradicate it and what we need to do to get that done! One thing you must have understood by now is that phishing will exist as long as we humans continue to utilize emails. It’s a double whammy both from the technological side as well as the psychological side. As a cybersecurity professional I would advise the following good practices to avoid falling for phishing attacks:- Now, if you read the above points and you are able to properly implement them it will keep you secure from every single phishing attack that you might face. The issue is that most people already know these but they feel it to be a hassle every time they have to check these things while using their email. So now let me give you other solutions which aren’t exactly hassle-free but they will help you if you are not able to follow the tips mentioned above and they can also protect you against advanced levels of phishing attacks too. Conclusion If you manage to follow these rules that I just mentioned you should be secure even against the most targeted and advanced phishing attacks and maybe just because of that won’t lose out on thousands of dollars of worth of NFTs, cryptos, and other extremely important personal data. If you think you need more help on this or you need to make your company members aware of these points, feel free to reach out to us. Let us help you up to your security game and make your business and startup feel more trustworthy to your customers. We are eagerly waiting for your call! Reach out to us at SECUREU & let’s
Protecting your mail like a PRO !!! Read More »
Protecting your mail like a PRO !!! To be true as a tech enthusiast who has been tinkering around with computers longer than I can remember, typing out this blog seems kind of ridiculous. I nearly moved away from my desk and had dropped the idea of writing this but then this happened. The podcast that I listen to occasionally started discussing the hacks that have been going around. You might say it’s a coincidence but right then they started discussing this major email-based phishing attack that was carried out against OpenSea users who bought NFTs on their platform. The attackers had sent an email to the customers of OpenSea that seemed legit at first glance and asked them to migrate their listings with the added bonus of gas-free transactions. If you know anything about the crypto world you know that gas fees (the cost of computing to carry out a transaction) can be pretty high and this bait of “gas-free” migration tempted users to fall for the trap and they ended up losing their NFTs. The total amount of the NFTs that was lost was worth around 1.7 million US dollars. It was then that I realized no matter how many blogs are already up there on the web regarding this. I am going to write one more, to maybe better educate my regular blog readers. Why does phishing exist in the first place? It’s 2022, on one side tech folks are busy creating Web3.0 infrastructure and then there are people still falling for phishing attacks that belong to the Web1.0 days. This begs us to ask the question why do phishing attacks still work in this day and age? People need to understand that email-based phishing attacks still exist cause email as technology was built with trust as an inherent factor. It was built in the early days of the internet when there were only a handful of people using it. They never saw the potential of what email could be and hence they never developed it keeping in mind the millions of spam emails that traverse the internet on a daily basis.It would have been fine if only that was the issue, but then comes in the other reason that’s a bigger contributing factor to why phishing attacks still persist. The reason is that we humans as a species are by default encoded to trust others rather than be suspicious of them. It is only after several mishaps that we learn that goes against our nature and start being suspicious of things that happen around us. So if you ever find yourself shocked by listening to the extent of phishing attacks that are still prevalent in 2022, remember the points that I just mentioned above. “I won’t fall for it” syndrome! One other issue that I have faced when it comes to phishing attacks is that people somehow disregard other peoples’ experiences and think that for some reason they are not vulnerable to such attacks and will easily be able to detect them. Now, read the next few words very carefully. “You are as likely to be vulnerable to a phishing attack just like any other person on this earth”. Please get rid of the “I won’t fall for it” syndrome. People who have written books on phishing attacks and such schemes have failed to detect phishing attacks and fall for it themselves. Side Note: I myself have been duped of a hefty sum of money. They used one of my shortcomings against me. I was unemployed at the time and they somehow managed to convince me to pay them upfront as they can help me land a respectful job. Thinking about it today makes me laugh at how I could have fallen for it. So, trust me when I say greed & fear will somehow make you do things that you can’t even imagine yourself doing in the future. So let me reiterate that it is only when you understand your own shortcomings that you have any chance to securely navigate through the spam and malicious mail that floods your inbox on a regular basis. Now let’s try and find a solution for it! What should we do then? I am glad you asked, now that you properly understand why phishing still exists. Let’s dive into how can we really eradicate it and what we need to do to get that done! One thing you must have understood by now is that phishing will exist as long as we humans continue to utilize emails. It’s a double whammy both from the technological side as well as the psychological side. As a cybersecurity professional I would advise the following good practices to avoid falling for phishing attacks:- Now, if you read the above points and you are able to properly implement them it will keep you secure from every single phishing attack that you might face. The issue is that most people already know these but they feel it to be a hassle every time they have to check these things while using their email. So now let me give you other solutions which aren’t exactly hassle-free but they will help you if you are not able to follow the tips mentioned above and they can also protect you against advanced levels of phishing attacks too. Conclusion If you manage to follow these rules that I just mentioned you should be secure even against the most targeted and advanced phishing attacks and maybe just because of that won’t lose out on thousands of dollars of worth of NFTs, cryptos, and other extremely important personal data. If you think you need more help on this or you need to make your company members aware of these points, feel free to reach out to us. Let us help you up to your security game and make your business and startup feel more trustworthy to your customers. We are eagerly waiting for your call! Reach out to us at SECUREU & let’s